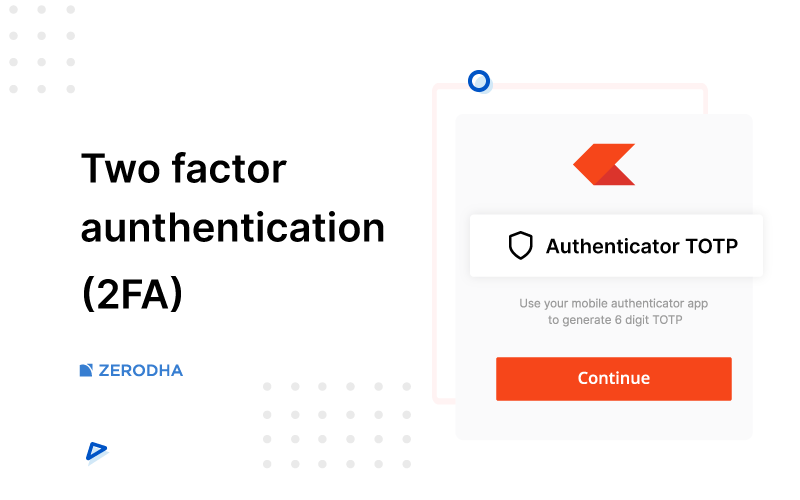
Two step authentication, 2-step Verification SMS code password concept. Smartphone with special 2FA software and tablet pc with multi-factor authentication safety and secure login form Stock Photo by ©bestforbest 353258856

Traditional Two-Factor Authentication vs. Beyond Identity's Passwordless Authentication | Beyond Identity


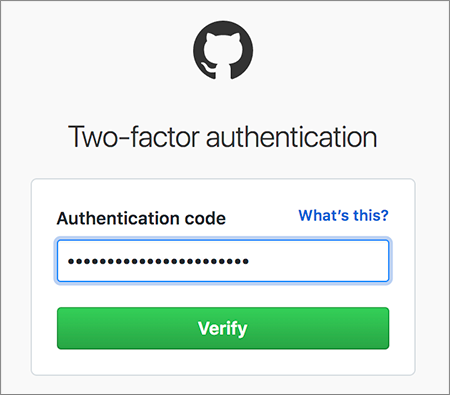



:max_bytes(150000):strip_icc()/007-turn-on-two-factor-authentication-facebook-4767863-5c8fc747bbdb4bfa9e4c24247177d710.jpg)
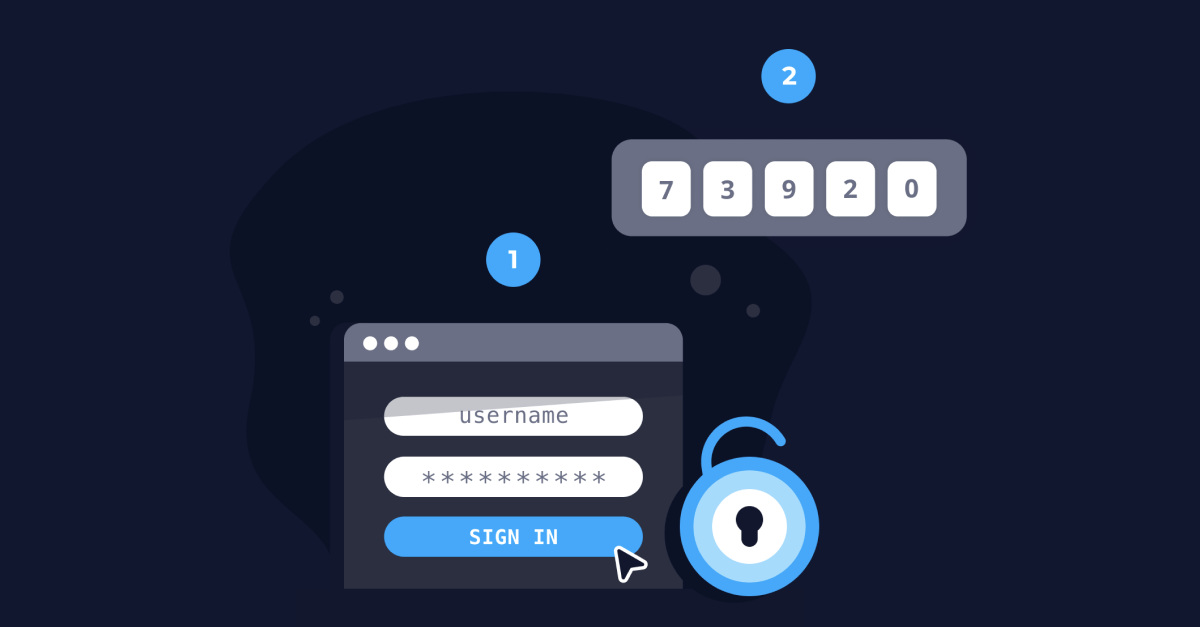
:max_bytes(150000):strip_icc()/twofactor-authentication-2fa.asp-final-5dc205d2a08b447abfb2e15eb131e28e.png)
![Is it OK to use text messages for 2-factor authentication? [Ask ZDNet] | ZDNET Is it OK to use text messages for 2-factor authentication? [Ask ZDNet] | ZDNET](https://www.zdnet.com/a/img/resize/d98bbe8f0d4626a2b97edc9de73482a10e73b7b5/2022/03/31/bdec141b-ec57-4272-a201-b74bf3618de0/gettyimages-1311125874-2fa-text2two-steps-authentication-verification-code-message-on-smartphone.jpg?auto=webp&fit=crop&height=900&width=1200)